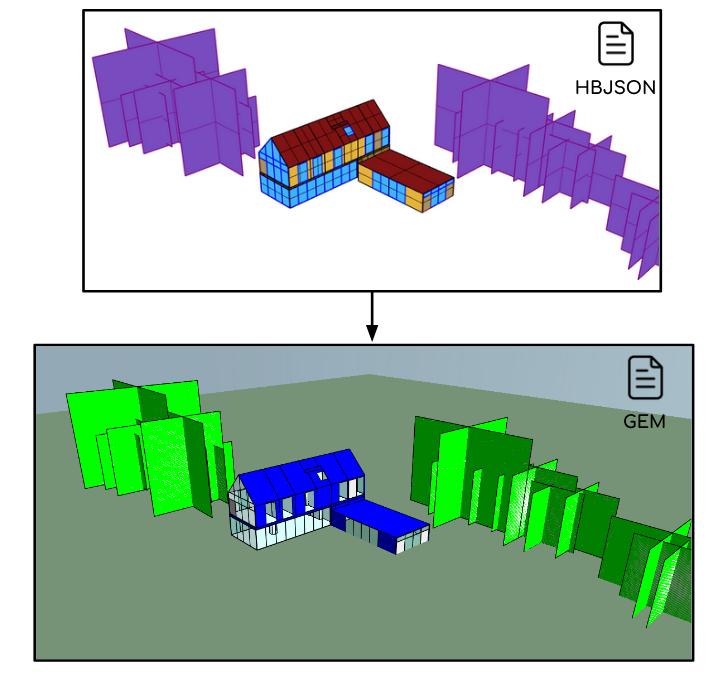
honeybee-ies
Honeybee extension for export a HBJSON file to IES-VE GEM file format
Installation
pip install honeybee-ies
QuickStart
import pathlib
from honeybee.model import Model
path_to_hbjson = './tests/assets/sample_model_45.hbjson'
path_to_out_folder = pathlib.Path('./tests/assets/temp')
path_to_out_folder.mkdir(parents=True, exist_ok=True)
model = Model.from_hbjson(path_to_hbjson)
# the to_gem method is added to model by honeybee-ies library
gem_file = model.to_gem(path_to_out_folder.as_posix(), name='sample_model_45')
You can also run the command from CLI
honeybee-ies translate model-to-gem ./tests/assets/revit_sample_model.hbjson --name revit-sample-model
API Documentation
Local Development
- Clone this repo locally
git clone [email protected]:ladybug-tools/honeybee-ies
# or
git clone https://github.com/ladybug-tools/honeybee-ies
- Install dependencies:
cd honeybee-ies
pip install -r dev-requirements.txt
pip install -r requirements.txt
- Run Tests:
python -m pytest tests/
- Generate Documentation:
sphinx-apidoc -f -e -d 4 -o ./docs ./honeybee_ies
sphinx-build -b html ./docs ./docs/_build/docs