Filter By
1031 Repositories
Python
Cowrie SSH/Telnet Honeypot https://cowrie.readthedocs.io
Cowrie Welcome to the Cowrie GitHub repository This is the official repository for the Cowrie SSH and Telnet Honeypot effort. What is Cowrie Cowrie is

Infection Monkey - An automated pentest tool
Infection Monkey Data center Security Testing Tool Welcome to the Infection Monkey! The Infection Monkey is an open source security tool for testing a
A black hole for Internet advertisements
Network-wide ad blocking via your own Linux hardware The Pi-hole® is a DNS sinkhole that protects your devices from unwanted content, without installi

xp_CAPTCHA(白嫖版) burp 验证码 识别 burp插件
xp_CAPTCHA(白嫖版) 说明 xp_CAPTCHA (白嫖版) 验证码识别 burp插件 安装 需要python3 小于3.7的版本 安装 muggle_ocr 模块(大概400M左右) python3 -m pip install -i http://mirrors.aliyun.com/
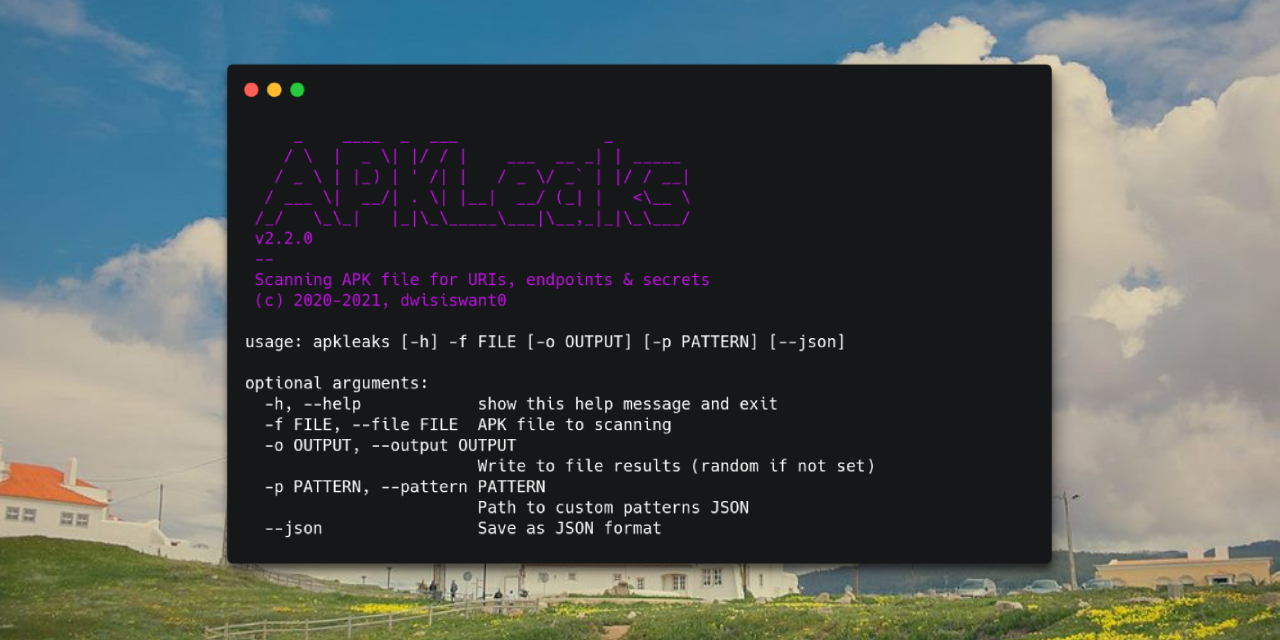
APKLeaks - Scanning APK file for URIs, endpoints & secrets.
APKLeaks - Scanning APK file for URIs, endpoints & secrets.

信息收集自动化工具
水泽-信息收集自动化工具 郑重声明:文中所涉及的技术、思路和工具仅供以安全为目的的学习交流使用,任何人不得将其用于非法用途以及盈利等目的,否则后果自行承担。 0x01 介绍 作者:Ske 团队:0x727,未来一段时间将陆续开源工具,地址:https://github.com/0x727 定位:协助
Dumping revelant information on compromised targets without AV detection
DonPAPI Dumping revelant information on compromised targets without AV detection DPAPI dumping Lots of credentials are protected by DPAPI (link ) We a
Searches through git repositories for high entropy strings and secrets, digging deep into commit history
truffleHog Searches through git repositories for secrets, digging deep into commit history and branches. This is effective at finding secrets accident
Automatic SQL injection and database takeover tool
sqlmap sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of
A Python tool to automate some dorking stuff to find information disclosures.
WebDork v1.0.3 A open-source tool to find publicly available sensitive information about Companies/Organisations! WebDork A Python tool to automate so

MozDef: Mozilla Enterprise Defense Platform
MozDef: Documentation: https://mozdef.readthedocs.org/en/latest/ Give MozDef a Try in AWS: The following button will launch the Mozilla Enterprise Def

Privacy-respecting metasearch engine
Privacy-respecting, hackable metasearch engine / pronunciation səːks. If you are looking for running instances, ready to use, then visit searx.space.
SpiderFoot automates OSINT collection so that you can focus on analysis.
SpiderFoot is an open source intelligence (OSINT) automation tool. It integrates with just about every data source available and utilises a range of m

MVT is a forensic tool to look for signs of infection in smartphone devices
Mobile Verification Toolkit Mobile Verification Toolkit (MVT) is a collection of utilities to simplify and automate the process of gathering forensic
Let's you scan the entire internet in a couple of hours and identify all Minecraft servers on IPV4
Minecraft-Server-Scanner Let's you scan the entire internet in a couple of hours and identify all Minecraft servers on IPV4 Installation and running i
Mr.Holmes is a information gathering tool (OSINT)
🔍 Mr.Holmes Mr.Holmes is a information gathering tool (OSINT). Is main purpose is to gain information about domains,username and phone numbers with t

NEW FACEBOOK CLONER WITH NEW PASSWORD, TERMUX FB CLONE, FB CLONING COMMAND. M
NEW FACEBOOK CLONER WITH NEW PASSWORD, TERMUX FB CLONE, FB CLONING COMMAND. M
This repository contains wordlists for each versions of common web applications and content management systems (CMS). Each version contains a wordlist of all the files directories for this version.
webapp-wordlists This repository contains wordlists for each versions of common web applications and content management systems (CMS). Each version co
Quickstart resources for the WiFi Nugget, a cat themed WiFi Security platform for beginners.
Quickstart resources for the WiFi Nugget, a cat themed WiFi Security platform for beginners.
POC for detecting the Log4Shell (Log4J RCE) vulnerability
Interactsh An OOB interaction gathering server and client library Features • Usage • Interactsh Client • Interactsh Server • Interactsh Integration •

Lnkbomb - Malicious shortcut generator for collecting NTLM hashes from insecure file shares
Lnkbomb Lnkbomb is used for uploading malicious shortcut files to insecure file

ClusterFuzz is a scalable fuzzing infrastructure that finds security and stability issues in software.
ClusterFuzz ClusterFuzz is a scalable fuzzing infrastructure that finds security and stability issues in software. Google uses ClusterFuzz to fuzz all
Open Source Intelligence gathering tool aimed at reducing the time spent harvesting information from open sources.
The Recon-ng Framework Recon-ng content now available on Pluralsight! Recon-ng is a full-featured reconnaissance framework designed with the goal of p
🍉一款基于Python-Django的多功能Web安全渗透测试工具,包含漏洞扫描,端口扫描,指纹识别,目录扫描,旁站扫描,域名扫描等功能。
Sec-Tools 项目介绍 系统简介 本项目命名为Sec-Tools,是一款基于 Python-Django 的在线多功能 Web 应用渗透测试系统,包含漏洞检测、目录识别、端口扫描、指纹识别、域名探测、旁站探测、信息泄露检测等功能。本系统通过旁站探测和域名探测功能对待检测网站进行资产收集,通过端
A high-performance DNS stub resolver for bulk lookups and reconnaissance (subdomain enumeration)
MassDNS A high-performance DNS stub resolver MassDNS is a simple high-performance DNS stub resolver targeting those who seek to resolve a massive amou
BloodyAD is an Active Directory Privilege Escalation Framework
BloodyAD Framework BloodyAD is an Active Directory Privilege Escalation Framework, it can be used manually using bloodyAD.py or automatically by combi
Agile Threat Modeling Toolkit
Threagile is an open-source toolkit for agile threat modeling:
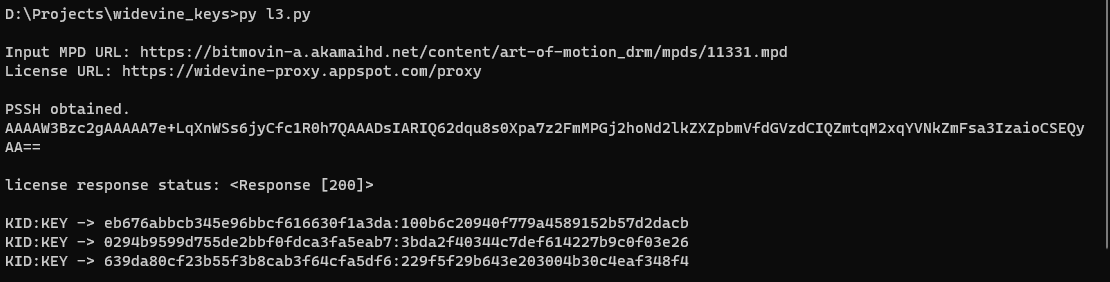
This repo created for bypassing Widevine L3 DRM and obtaining keys.
First run: Copy headers (with cookies) of POST license request from browser to headers.py like dictionary. pip install -r requirements.txt # if doesn'