HashDB IDA Plugin
Malware string hash lookup plugin for IDA Pro. This plugin connects to the OALABS HashDB Lookup Service.
Adding New Hash Algorithms
The hash algorithm database is open source and new algorithms can be added on GitHub here. Pull requests are mostly automated and as long as our automated tests pass the new algorithm will be usable on HashDB within minutes.
Using HashDB
HashDB can be used to look up strings that have been hashed in malware by right-clicking on the hash constant in the IDA disassembly view and launching the HashDB Lookup client.
Settings
Before the plugin can be used to look up hashes the HashDB settings must be configured. The settings window can be launched from the plugins menu Edit->Plugins->HashDB.
Hash Algorithms
Click Refresh Algorithms to pull a list of supported hash algorithms from the HashDB API, then select the algorithm used in the malware you are analyzing.
Optional XOR
There is also an option to enable XOR with each hash value as this is a common technique used by malware authors to further obfuscate hashes.
API URL
The default API URL for the HashDB Lookup Service is https://hashdb.openanalysis.net/. If you are using your own internal server this URL can be changed to point to your server.
Enum Name
When a new hash is identified by HashDB the hash and its associated string are added to an enum in IDA. This enum can then be used to convert hash constants in IDA to their corresponding enum name. The enum name is configurable from the settings in the event that there is a conflict with an existing enum.
Hash Lookup
Once the plugin settings have been configured you can right-click on any constant in the IDA disassembly window and look up the constant as a hash. The right-click also provides a quick way to set the XOR value if needed.
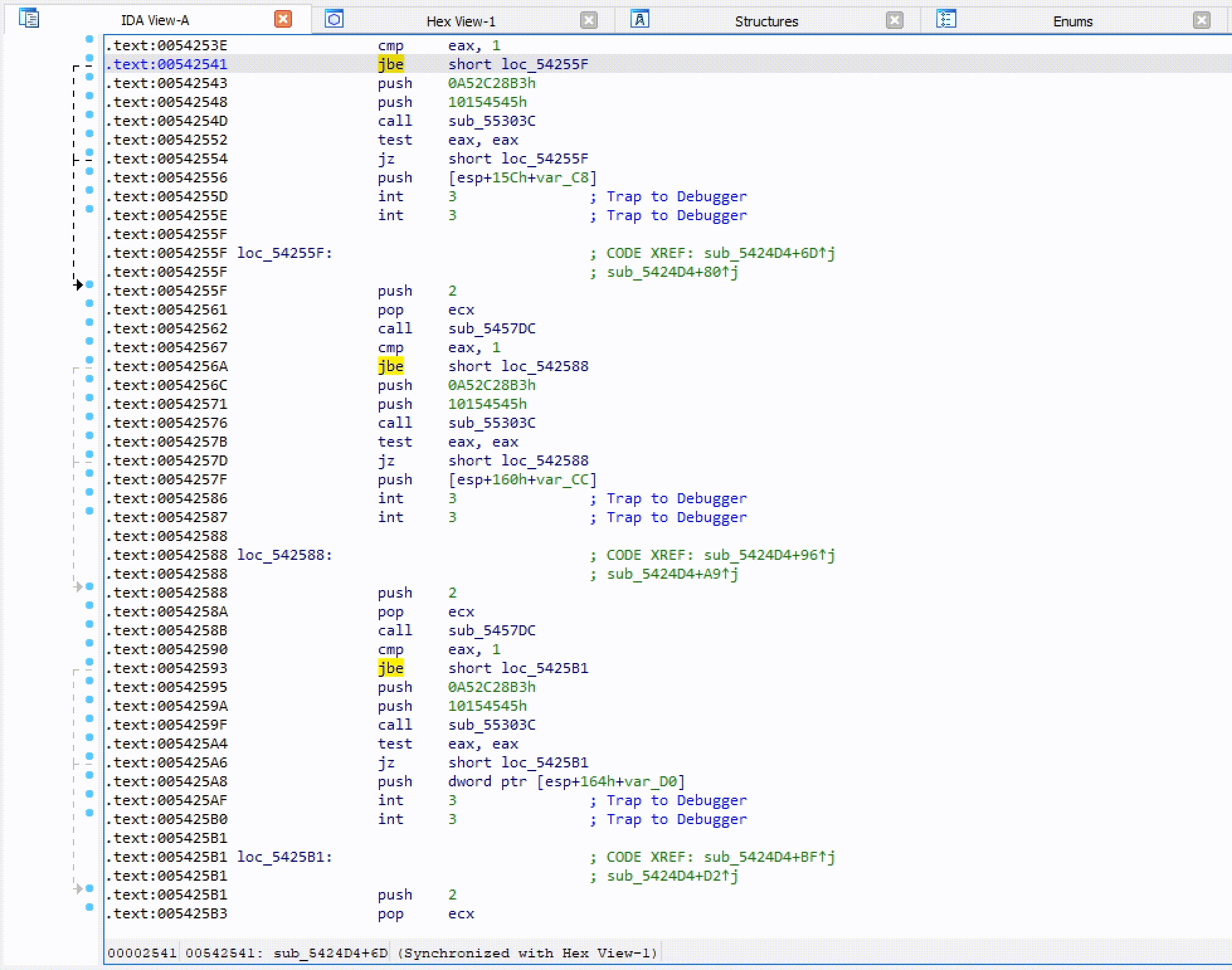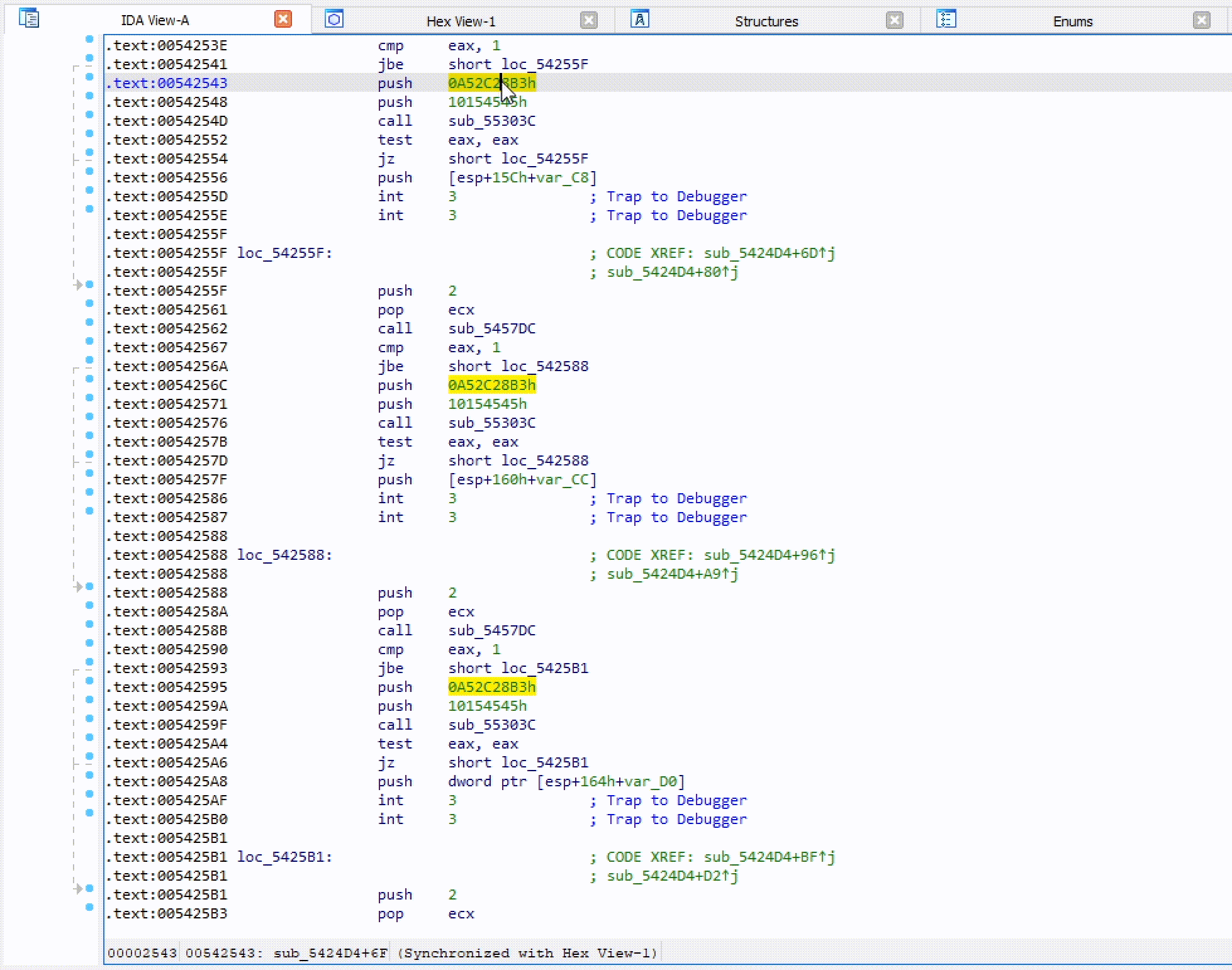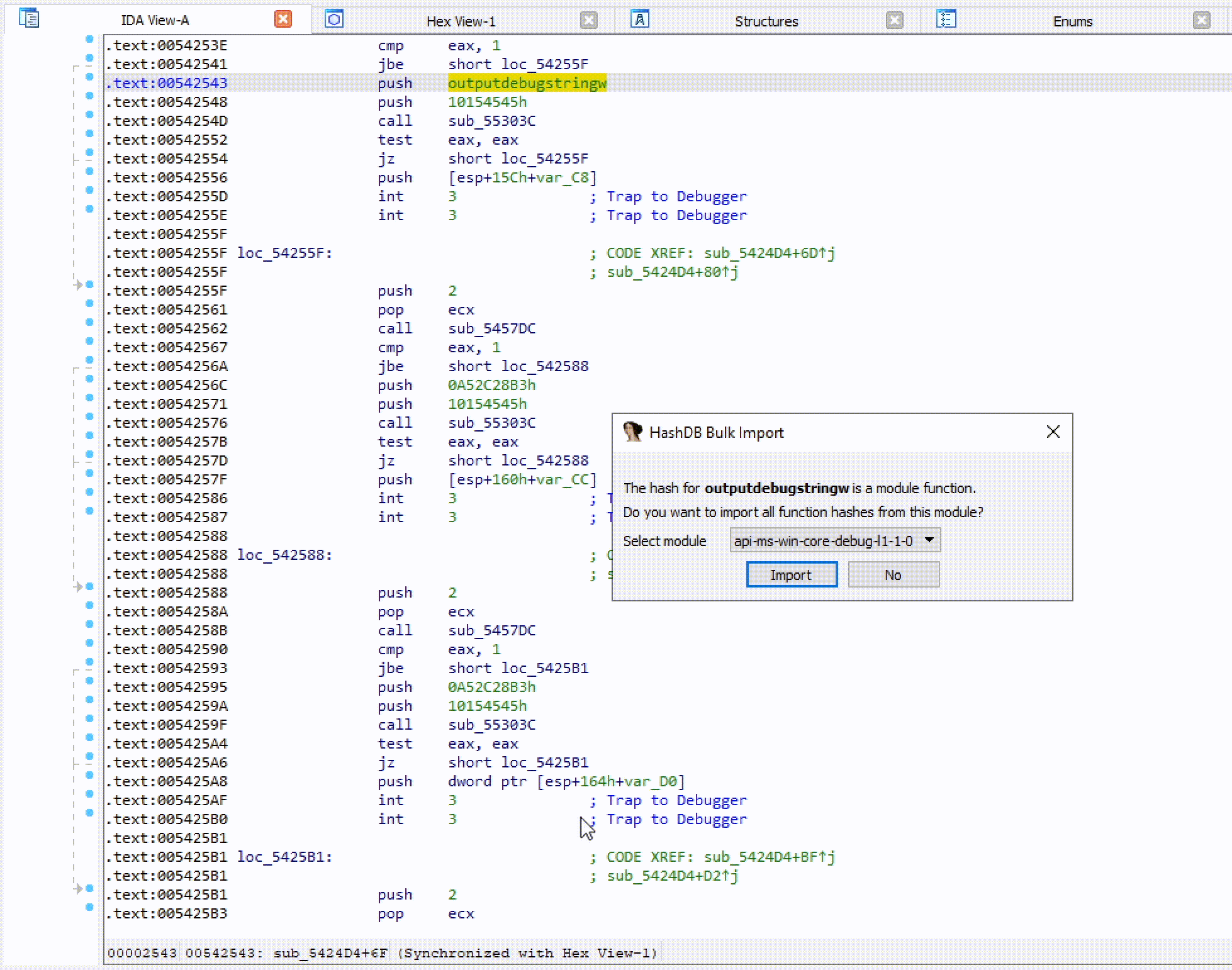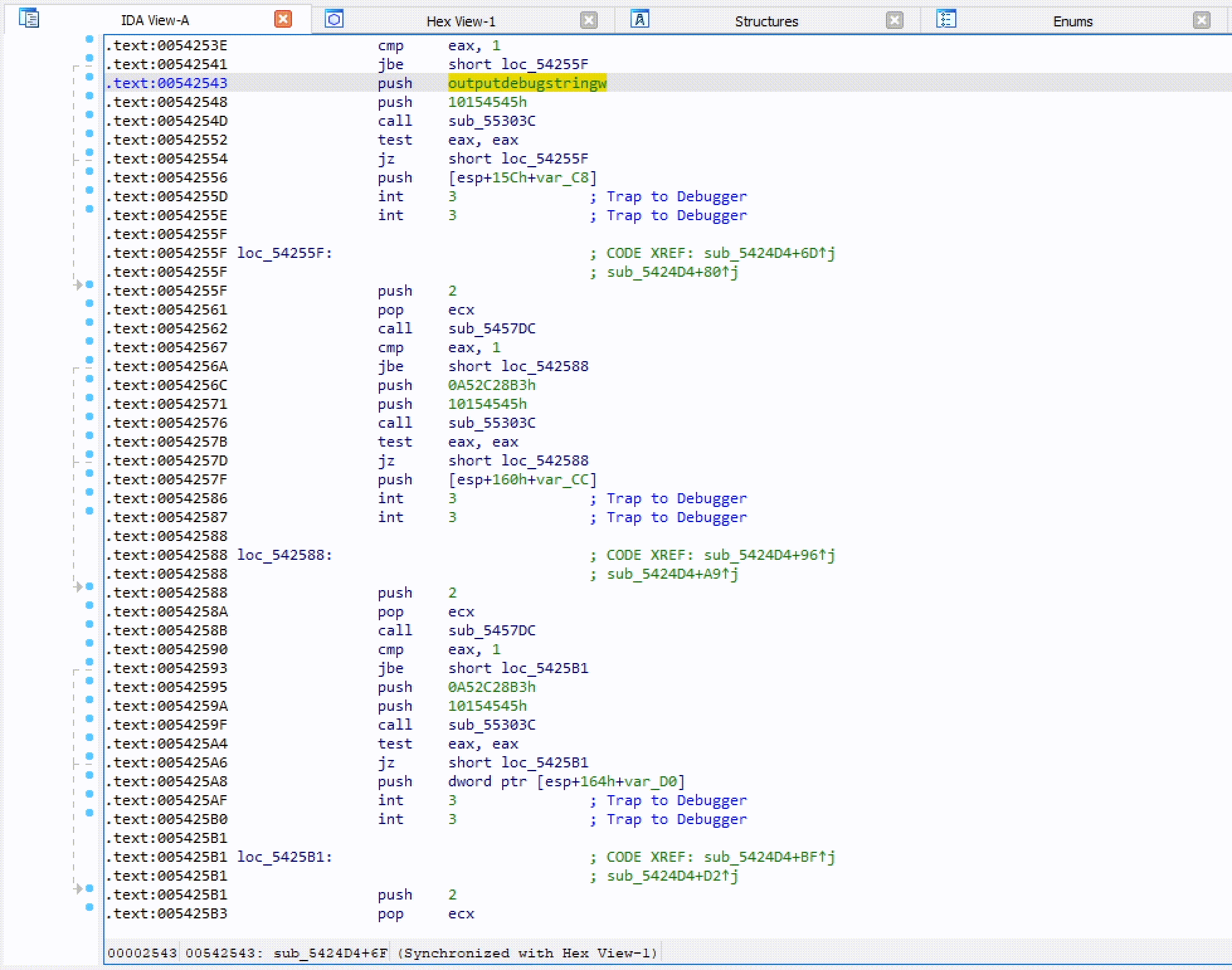
Bulk Import
If a hash is part of a module a prompt will ask if you want to import all the hashes from that module. This is a quick way to pull hashes in bulk. For example, if one of the hashes identified is Sleep from the kernel32 module, HashDB can then pull all the hashed exports from kernel32.
Installing HashDB
Before using the plugin you must install the python requests module in your IDA environment. The simplest way to do this is to use pip from a shell outside of IDA.
pip install requests
Once you have the requests module installed simply copy the latest release of hashdb.py into your IDA plugins directory and you are ready to start looking up hashes!
❗
Compatibility Issues
The HashDB plugin has been developed for use with the IDA 7+ and Python 3 it is not backwards compatible.







 "
"


